Unlocking the Power of Software Defined Storage
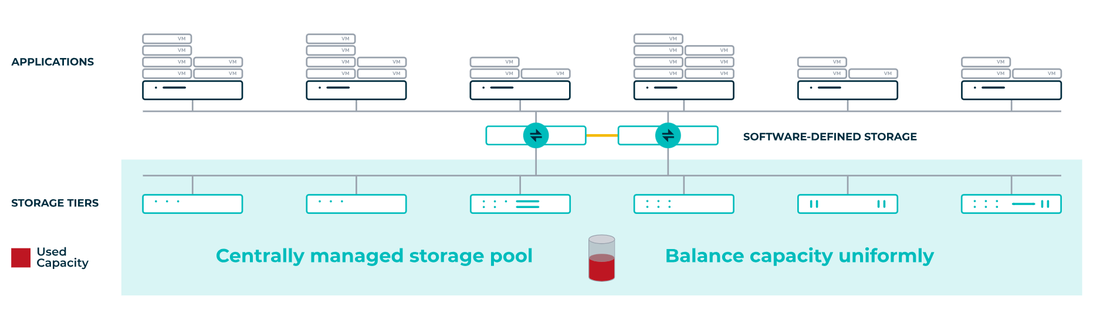
Image Source: Datacore Understanding Software Defined Storage Software Defined Storage (SDS) is a data storage architecture that differentiates the control plane from the data plane.…

Image Source: Datacore Understanding Software Defined Storage Software Defined Storage (SDS) is a data storage architecture that differentiates the control plane from the data plane.…

Managing and storing massive amounts of data has become critical for organizations in today's digital era. Traditional centralized storage systems often need help to cope…

In today's fast-paced digital landscape, businesses constantly seek ways to increase efficiency, reduce costs, and deliver exceptional customer service. One area that holds immense potential…
When it comes to network disasters, no one wants to be the first in line for a wild ride. But despite its unfortunate inevitability, your…

We all know that storage isn't the most attractive component in IT - far from it. But, when deployed correctly and configured sensibly, it can…

In our current digital age, data backup is something that all business leaders and professionals should be paying attention to. All organizations are at risk…

Storage is Getting Smarter Our civilization’s been veering towards intelligence all this time. And our storage infrastructures are keeping up by developing intelligence of their…

Cloud Storage, a Great Choice A 21st-century industry looking for uncompromising scalability and performance cannot possibly come across Cloud Storage and say, “I’ll pass.” Be…

Data plays a crucial part in our modern communication world and daily life. As the usage of our data increases, exponential, users and customers are…

The toughest Terminator, T-1000 can demonstrate rapid shapeshifting, near-perfect mimicry, and recovery from damage. This is because it is made of mimetic polyalloy with robust…

AWS S3 compatible storage is one of the emerging technologies in the enterprise storage medium. Initially, it was used only by Amazon in public cloud…

What is NVMe? NVMe is the new protocol which is known as Non Volatile Memory Express. Let’s have a brief idea about volatile and non-volatile…