Empowering Innovation or Risky Business? Citizen Development vs. Shadow IT- A Complete Guide

Audio : Listen to This Blog.
Citizen Development and Shadow IT are two distinct approaches to meeting the technology needs of organizations. Understanding the differences between these two concepts is crucial for organizations to effectively leverage their benefits and mitigate potential risks. In this article, we will delve into the world of Citizen Development and Shadow IT, explore their characteristics, benefits, and challenges, and discuss strategies to embrace Citizen Development while minimizing the use of Shadow IT.
Understanding Citizen Development
The concept of Citizen Development revolves around empowering non-technical employees to create applications or perform customizations using low-code or no-code platforms. These platforms provide intuitive interfaces and pre-built modules that allow individuals to build applications without deep coding knowledge.
The Concept of Citizen Development

Citizen Development represents a paradigm shift where technical expertise is no longer limited to IT departments. By enabling employees from various departments to contribute to application development, organizations can tap into a wider pool of talent and foster innovation.
Benefits of Citizen Development
Organizations embracing Citizen Development can benefit from increased agility, as employees can create applications that address their specific needs in a timely manner. This can lead to improved productivity, enhanced collaboration, and better customer experiences.
Moreover, Citizen Development encourages a sense of ownership and empowerment among employees, as they directly contribute to solving business challenges. This can boost employee morale and foster a culture of innovation within the organization.
Potential Risks and Challenges of Citizen Development
While Citizen Development offers numerous advantages, organizations must be mindful of potential risks and challenges. One of the key concerns is the potential for creating applications that lack proper security measures or adhere to data privacy regulations. It is essential to provide training and guidance to Citizen Developers to ensure they understand the importance of securely handling sensitive information.
Another challenge organizations might face is maintaining the quality and integrity of applications created by Citizen Developers. Organizations should establish governance frameworks to review and validate applications, ensuring they meet the necessary standards and align with business objectives.
Ensuring Collaboration and Knowledge Sharing
One of the key aspects of successful Citizen Development is fostering collaboration and knowledge sharing among employees. Organizations can create dedicated forums or communities where Citizen Developers can connect, share ideas, and seek advice from their peers. This not only enhances the learning experience but also encourages the exchange of best practices and innovative solutions. Furthermore, organizations can organize regular meetups or workshops where Citizen Developers can showcase their applications and share their success stories. This not only boosts morale but also inspires others to explore their creativity and contribute to the development of new applications.
Supporting Continuous Learning and Skill Development
As technology evolves rapidly, it is crucial for Citizen Developers to continuously update their skills and stay abreast of the latest trends in low-code or no-code platforms. Organizations can provide training programs, online courses, or even certifications to help Citizen Developers enhance their technical knowledge and proficiency.
In addition to technical skills, organizations should also encourage Citizen Developers to develop a deeper understanding of the business processes and objectives. This will enable them to create applications that are not only technically sound but also aligned with the strategic goals of the organization.
Expanding the Scope of Citizen Development
While Citizen Development initially focused on creating applications, organizations are now exploring its potential in other areas as well. For example, Citizen Development can be extended to data analysis, where non-technical employees can leverage self-service analytics tools to gain insights and make data-driven decisions.
Furthermore, organizations can encourage Citizen Developers to contribute to process automation, allowing them to identify repetitive tasks and automate them using workflow automation tools. This not only improves efficiency but also frees up employees’ time to focus on more strategic and value-added activities.
Diving into Shadow IT

Source : KissFlow
Shadow IT refers to the use of unauthorized software or IT infrastructure by employees, without the knowledge or approval of the IT department. It often arises from a desire for flexibility, faster solutions, or circumventing perceived bureaucratic processes.
Exploring the world of Shadow IT unveils a complex landscape where employees navigate between official protocols and personal preferences. The allure of autonomy in choosing tools and technologies can sometimes lead individuals down the path of unauthorized software usage, creating a parallel IT environment within organizations.
Defining Shadow IT
Shadow IT encompasses various activities such as employees using personal communication tools for work-related purposes, adopting cloud services without IT’s approval, or using unlicensed software. It poses risks to data security, compliance, and overall IT governance.
Within the realm of Shadow IT, employees often find themselves at a crossroads between expediency and adherence to organizational policies. The allure of quick solutions and personalized workflows can sometimes overshadow the potential risks associated with unauthorized software usage.
Why Employees Resort to Shadow IT
Employees resort to Shadow IT for several reasons. They might feel restricted by the limitations of approved software or experience delays in IT support for their technology needs. Additionally, some employees may have personal preferences for tools or applications they find more user-friendly or convenient.
The siren call of Shadow IT beckons employees seeking agility and customization in their work processes. The need for immediate solutions and the quest for enhanced productivity often drive individuals to explore uncharted technological territories, albeit at the cost of organizational oversight.
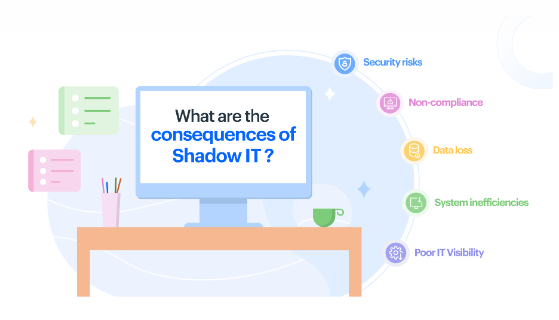
The Dangers of Shadow IT
Source : KissFlow
Shadow IT introduces several risks to organizations. It can lead to data breaches, as unauthorized software may not have the necessary security measures in place. Compatibility issues, lack of integration with existing systems, and unmanaged licenses are among the many challenges organizations face due to Shadow IT.
Delving deeper into the shadows of unauthorized IT usage unveils a host of perils lurking beneath the surface. The specter of data vulnerability, system incompatibility, and regulatory non-compliance looms large, casting a shadow over the seamless functioning of organizational IT infrastructures.
Comparing Citizen Development and Shadow IT
While Citizen Development and Shadow IT both involve employees creating solutions outside the traditional IT framework, they serve different purposes and have distinct implications for organizations.
When it comes to Citizen Development, it is a structured approach that empowers employees to create applications or tools within a framework approved by the IT department. On the other hand, Shadow IT refers to the unauthorized use of IT systems or solutions without the knowledge or approval of the IT department. This often occurs when employees seek quick fixes or workarounds to address immediate needs, bypassing formal IT channels. While Shadow IT can sometimes result in innovative solutions, it poses significant risks in terms of data security, compliance, and integration with existing systems. Organizations must carefully manage and monitor Shadow IT activities to mitigate these risks effectively.
Similarities Between Citizen Development and Shadow IT
Both Citizen Development and Shadow IT arise from the need for employees to address their technology requirements independently. They can provide quick solutions and enable faster response times compared to traditional IT processes. However, it is essential to differentiate between the two approaches to ensure that proper governance is in place.
Despite their differences, both Citizen Development and Shadow IT underscore the importance of agility and innovation in today’s rapidly evolving digital landscape. By understanding the nuances of each approach and implementing appropriate governance measures, organizations can harness the potential of employee-driven technology initiatives while safeguarding against potential risks and ensuring alignment with strategic objectives.
Key Differences and Their Implications
The key difference between Citizen Development and Shadow IT lies in the level of control and oversight. Citizen Development encourages collaboration and aligns with organizational objectives, allowing IT to maintain visibility and steer the development process. In contrast, Shadow IT operates outside the purview of IT, potentially increasing security risks and hindering integration.
Furthermore, Citizen Development promotes a culture of transparency and knowledge sharing within the organization, enabling cross-functional teams to work together towards common goals. This collaborative approach not only enhances the quality of solutions but also fosters a sense of ownership and accountability among employees. In contrast, Shadow IT can lead to siloed efforts and fragmented systems, creating inefficiencies and complicating IT management.
Building vs. Breaking the Rules
Governance plays a crucial role in both Citizen Development and Shadow IT, shaping the outcomes and impact on organizations.
The Role of Governance in Citizen Development
A well-defined governance framework is essential to ensure the success of Citizen Development initiatives. It provides guidelines for employees engaging in Citizen Development and helps maintain alignment with organizational strategies and security requirements. By incorporating IT oversight, organizations can strike a balance between empowering employees and mitigating risks.
The Consequences of Rule-Breaking in Shadow IT
In Shadow IT, breaking the rules can have severe consequences. Unapproved software or systems may introduce vulnerabilities, violate compliance regulations, and impede interoperability with existing infrastructure. Organizations should clearly communicate the risks associated with Shadow IT and foster a culture that encourages open dialogue with the IT department.
Mitigating Risks and Maximizing Benefits
While embracing Citizen Development, organizations must proactively manage risks associated with Shadow IT to protect their data, maintain operational efficiency, and achieve the intended benefits.

Strategies for Encouraging Citizen Development
Organizations can establish centers of excellence to provide Citizen Developers with the necessary resources, training, and support. By fostering communities where Citizen Developers can share knowledge and best practices, organizations can harness the full potential of Citizen Development while minimizing the risks.
Ways to Minimize the Use of Shadow IT
To minimize the use of Shadow IT, organizations should emphasize the availability and benefits of approved software and IT solutions. Clear communication, providing timely IT support, and involving employees in the decision-making process can significantly reduce the inclination towards Shadow IT.
Conclusion
In conclusion, understanding the nuances of Citizen Development and Shadow IT is crucial for organizations to strike the right balance between empowering employees and maintaining control over technology processes. By embracing Citizen Development and implementing robust governance frameworks, organizations can leverage the benefits of self-service technology while minimizing the risks associated with Shadow IT.
